Azure Bastion – Securing Access to Virtual Networks
Azure Bastion
Traditionally, there were two main ways to connect to VMs in the cloud. The first was to assign a static public IP address and connect to them via the Remote Desktop Protocol (RDP) or secure shell (SSH), but this was later replaced by removing the public IP address and using a virtual private network (VPN) to securely connect to the server via the RDP or SSH. The Azure Bastion service enables you to connect to a VM by using your browser and the Azure portal instead of using technologies such as VPN. Bastion is a platform-as-a-service (PaaS) that you provision inside the VNet in Azure, which provides secure connectivity on management ports such as the RDP and SSH. Here are some key benefits of using Azure Bastion:
- The RDP and/or SSH directly in the Azure portal: An RDP or SSH session via the browser.
- Remote session via TLS: Bastion uses an HTML5-based web client that is streamed to the device, connecting to it via TLS on port 443 for security purposes.
- No public IP address required on a VM: Bastion will open an RDP/SSH connection to the VM by using the private IP address, meaning no public IP address is required.
- No additional firewall rules required: There are no additional complex NSG rules required for this solution to work; only allow Bastion to access the required VMs.
- Reduced attack surface: VMs are better protected, as there are no public IP addresses assigned to them, which means external malicious users cannot port-scan the VM to detect weaknesses in the VM.
The following is a diagram that shows how Azure Bastion works:
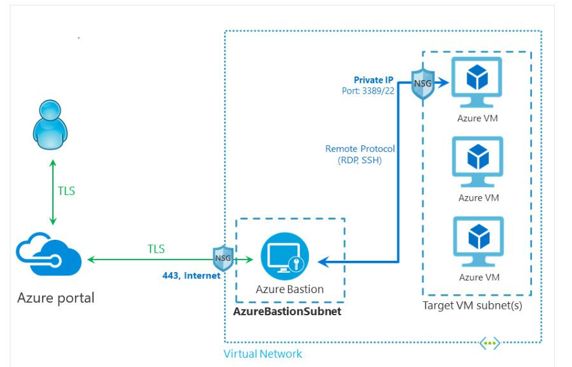
Figure 15.12 – How Azure Bastion works
Now that we have a better understanding of Azure Firewall and Azure Bastion, let’s learn how to do the following via PowerShell:
- Create a new VNet with a VM.
- Deploy an Azure Firewall.
- Create a default route within the firewall.
- Configure an application rule to allow access to www.google.com.
- Configure a network rule to allow access to external Domain Name System (DNS) servers.
- Test the firewall rules.
To achieve the preceding objectives, follow these steps:
- First, we need to connect to our Azure tenant by using the following PowerShell command:
Connect-AzAccount
The screenshot shows the output of the command:
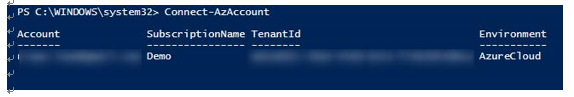
Figure 15.13 – Connecting to the Azure tenant via PowerShell
- If you have multiple subscriptions, you can use the following PowerShell command to select a specific subscription:
Select-AzSubscription -SubscriptionId “your-subscription-id”
- Now that we have selected our Azure tenant and subscription, let’s go ahead and create a new Resource Group (RG):
New-AzResourceGroup -Name Test-FW-RG -Location “East US”
The screenshot shows the successful creation of the new RG:
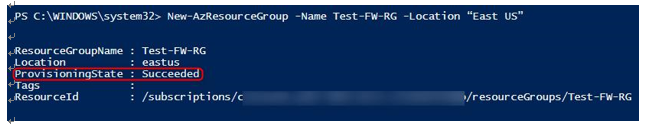
Figure 15.14 – Creating the new RG
- Next, we are going to create the VNet, which has three subnets — a bastion subnet, a firewall subnet, and the VM subnet:
$Bastionsub = New-AzVirtualNetworkSubnetConfig -Name AzureBastionSubnet -AddressPrefix 10.0.0.0/27
$FWsub = New-AzVirtualNetworkSubnetConfig -Name AzureFirewallSubnet -AddressPrefix 10.0.1.0/26
$VMSubnet = New-AzVirtualNetworkSubnetConfig -Name VMSubnet -AddressPrefix 10.0.2.0/24
$testVnet = New-AzVirtualNetwork -Name Test-FW-VN -ResourceGroupName Test-FW-RG -Location “East US” -AddressPrefix 10.0.0.0/16 -Subnet $Bastionsub, $FWsub, $VMSubnet
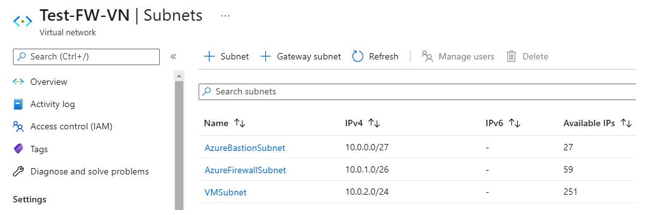
Figure 15.15 – A newly created VNet with the three subnets