Configuring Azure DNS – Implementing and Managing Virtual Networking
Configuring Azure DNS
Azure DNS is a hosting service for DNS domains where the name resolution is done via the Microsoft Azure infrastructure. It is important to note that you cannot buy domains via Azure DNS. However, you can delegate permissions to Azure DNS for record management.
There is also a feature called Azure Private DNS that provides a reliable and secure DNS service for VNets. When using private DNS zones, you can use a custom domain name instead of using the default domain names provided by Azure. One of the main reasons for using Azure Private DNS is that the domain names in the VNet will be resolved without having to configure custom DNS on the VNet.
The following is a high-level overview of how Azure Private DNS works:
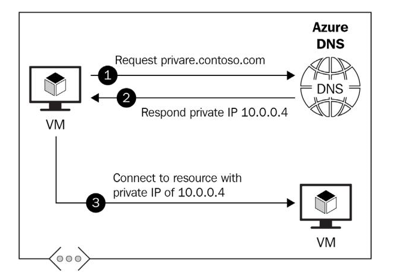
Figure 14.37 – Azure Private DNS
Important Note
Azure DNS does not support Domain Name Security Extensions (DNSSEC).
The following are some of the benefits of using Azure Private DNS:
• Removes the need for custom DNS solutions: DNS zones can be managed via native Azure infrastructure, which simplifies DNS configuration, since complex custom DNS solutions are no longer required.
• Supports common DNS record types: Azure DNS supports the following records –A, AAAA, CNAME, NX, PTR, SOA, SRV, and TXT.
• Automatic hostname record management: Azure automatically maintains hostname records for VMs within VNet.
• Hostname resolution between VNets
• Familiar tools and user experience: You can use the following to update DNS records– the Azure portal, PowerShell, the Azure CLI, ARM templates, and a REST API.
• Split-horizon DNS support: The creation of DNS zones with the same name that resolve to different IPs within a VNet and the internet.
• Availability: DNS private zones are available across all Azure regions and the Azure public cloud.
Let’s go ahead and configure Azure Private DNS via PowerShell using the following steps:
- In PowerShell, use the following command to connect to our Azure tenant:
Connect-AzAccount
- Next, we will need to install the Azure Private DNS module using the following command:
Install-Module -Name Az.PrivateDns -force
- Now, we need to create a new DNS zone using the following command. You will need to give it a name and point it to an existing RG:
$zone = New-AzPrivateDnsZone -Name demo.packt.com -ResourceGroupName VNet_Demo_ResourceGroup
- Lastly, we need to link the newly created DNS zone with a VNet using the following command. You will need to add your own RG name and VNet ID to link it to the correct VNet:
$link = New-AzPrivateDnsVirtualNetworkLink -ZoneName demo.packt.com `-ResourceGroupName VNet_Demo_ResourceGroup -Name “mylink” `-VirtualNetworkId /subscriptions/xxx/resourceGroups/ VNet_Demo_ResourceGroup/providers/Microsoft.Network/ virtualNetworks/DemoVNet -EnableRegistration
- Lastly, let’s confirm that our DNS zone has been created successfully. To do this, use the following PowerShell command:
Get-AzPrivateDnsZone -ResourceGroupName VNet_Demo_ ResourceGroup
The output of the command is shown in the following screenshot:
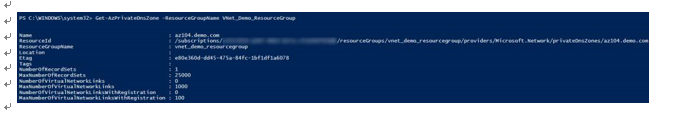
Figure 14.38 – Verifying that the private DNS zone has been created successfully
In this section, we had a look at what Azure DNS is and the difference between Azure DNS and Azure Private DNS. We also looked at how to configure a private DNS zone, link it to an existing VNet, and verify that it has been created successfully.
We encourage you to read up on Azure DNS further by using the following links:
• https://docs.microsoft.com/en-us/azure/dns/dns-overview
• https://docs.microsoft.com/en-us/azure/dns/private-dns-overview
Summary
In this chapter, we discussed how to create VNets including VNet peering, and how to configure private and public IP addresses and UDRs. We also had a look at subnetting in Azure and learned how to configure endpoints and private endpoints for VNets. Lastly, we looked at how Azure DNS works and configured a custom private DNS zone, linking it to an existing VNet via PowerShell.
Skills that students have gained after reading this chapter and following along with the hands-on demos include virtual networking, custom routing in Azure, securing resources via endpoints and private endpoints, and Azure DNS.
In the next chapter, we’ll cover how to secure access to VNets.